Securing your ERP system matters more than ever in today’s digital world. Cyber threats lurk around every corner, and they target the very backbone of your business operations.
You need reliable protection for sensitive data and smooth remote access. Understanding how to bolster your defences can help you safeguard critical information while enhancing overall security.
Ready to bulletproof your ERP system? Consider this your action plan for shoring up against any vulnerabilities that may threaten it.
Table of Content:
Table of Content

1. Exploring the Role of VPNs in ERP Security
Implementing a VPN can enhance your ERP system’s security to new heights. It serves as digital armor by encrypting your internet connection, making it significantly more difficult for hackers to breach. When used alongside the best ERP software, a VPN adds an extra layer of protection to sensitive business data, ensuring secure access for remote teams and safeguarding critical operations.
Remote work often means relying on networks that lack stringent security measures. These gaps are playgrounds for cybercriminals. But with a robust VPN, you’re constructing an impenetrable conduit for your data flow.
Set up policies that require all remote access through the VPN. Train employees to recognize phishing attempts and secure their devices before connecting to the network.
Regularly update your VPN software to maintain top-notch security standards.
By prioritizing these measures, you protect not just data but also the trust of clients who rely on your services and information every day.
2. Best Practices for Remote Access and Data Protection
Implementing robust security practices starts with choosing the right tools. Begin by using a reliable VPN to protect your ERP system, especially for remote access. You can test options like a free VPN trial by CyberGhost to evaluate its effectiveness before committing.
Ensure that all employees use this secure connection when accessing sensitive data outside the office. Additionally, clear policies should be established around password management and two-factor authentication to enhance security layers.
Regularly audit your systems and educate staff about potential threats, such as phishing scams. Conduct training sessions to help everyone recognize suspicious activity.
These steps lay a strong foundation for securing not only your data but also maintaining the integrity of your business operations overall.
3. Understanding Common Cyber Threats to ERP Systems
Cyber threats targeting ERP systems are diverse and constantly evolving. Here are some common types you should be aware of:
- Phishing Scams: Devious as they are, these tricks coax users into exposing critical information by masquerading as credible entities.
- Malicious Software: This digital poison can seep into your system, purloining data or disrupting your operations.
- Ransomware Incursions: An insidious form of digital extortion that barricades access to crucial data until you cough up a ransom.
- Internal Security Slips: Sometimes, the risk roams within your walls. Employees with access could unintentionally open the gates to breaches, whether through carelessness or deliberate acts.
To combat these threats, regularly update your software and conduct vulnerability assessments.
Fortify your defenses with robust passwords bolstered by multi-factor authentication – a formidable duo. Keeping abreast of emerging threats is equally critical to ensure your ERP system stands resilient in the dynamic terrain of digital security.
4. Integrating Multi-Factor Authentication into Your Strategy
By weaving multi-factor authentication (MFA) into your security fabric, you’re adding a vital shield to your ERP system. MFA elevates security protocols beyond mere password reliance, insisting on extra verification measures from users.
This could include:
- One-off text message codes.
- Biometric confirmations such as fingerprint or facial recognition scans.
- Personalized security questions with answers known solely to the user.
Embrace MFA and you materially slash the risk of unwelcome access; this holds true even if passwords fall into the wrong hands.
Any team member across the board is required to tap into sensitive data from afar.
Regularly review and update authentication methods as new technologies emerge. Emphasizing strong password policies alongside MFA creates a comprehensive security approach that protects your ERP system from evolving cyber threats while maintaining operational efficiency.
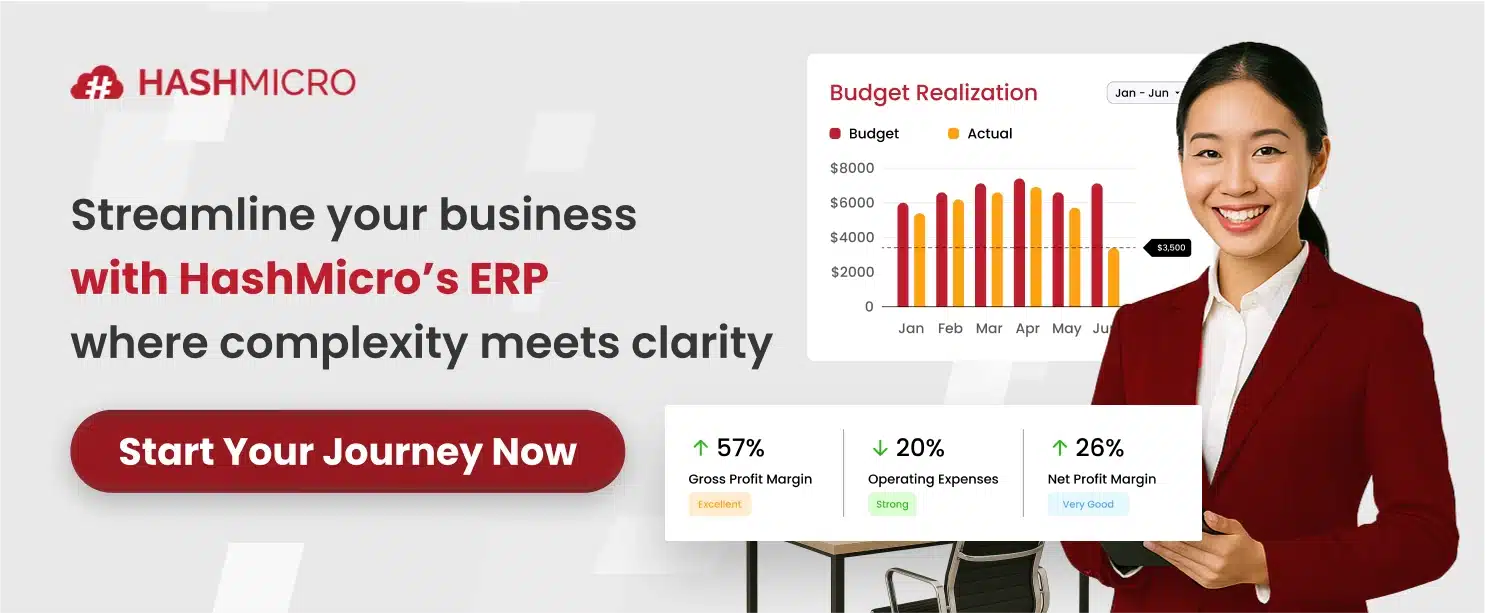
5. Adopt an ERP System with High Security
The ERP system you choose is crucial to establishing a secure foundation for your business operations. A robust ERP solution not only reduces security risks but also offers advanced protection against evolving threats. Opt for a system with proven security protocols and cutting-edge technology, like HashMicro ERP, one of Singapore’s leading ERP solutions.
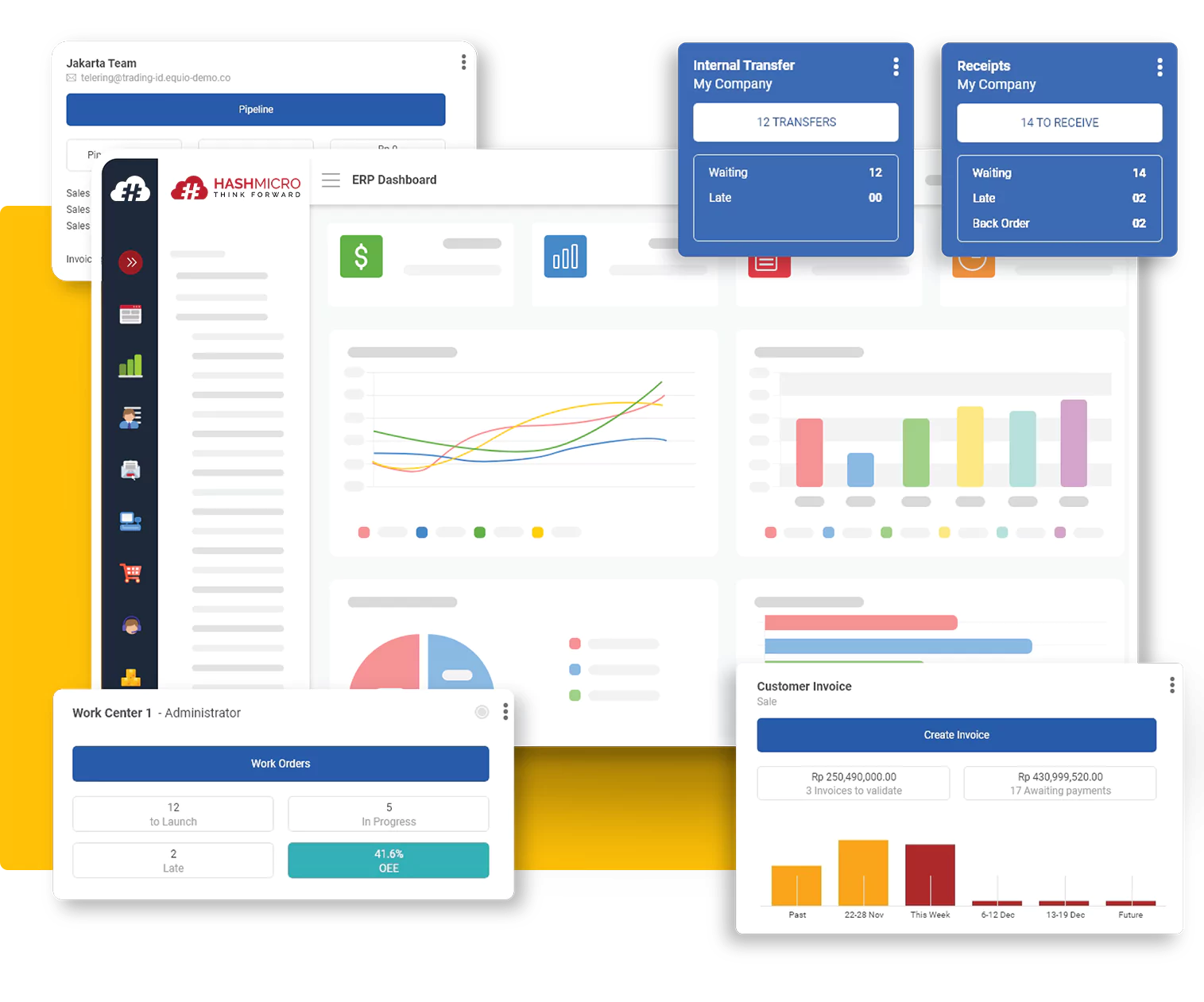
HashMicro ERP seamlessly integrates essential business functions into a single, fortified platform, providing heightened security, operational accuracy, and adaptability. Its secure infrastructure, coupled with comprehensive modules, ensures that sensitive data is protected and that operational processes remain smooth, efficient, and resilient against potential cyber threats.
Each module within HashMicro ERP is fortified with encryption, secure access controls, and continuous monitoring to prevent unauthorized data access. As a result, businesses can operate with peace of mind, knowing that their sensitive information is safeguarded against internal and external threats.
The system’s advanced security features include multi-factor authentication (MFA), role-based access, and end-to-end encryption, offering multiple layers of protection. HashMicro also emphasizes proactive security maintenance, regularly updating its software to counter the latest cyber threats and vulnerabilities.
By continually evolving with the cybersecurity landscape, HashMicro ERP ensures businesses stay one step ahead of cybercriminals. This commitment to cutting-edge security, combined with the system’s adaptability, makes HashMicro an ideal choice for businesses looking to improve efficiency while maintaining a strong defence against potential risks.
6. Cultivating a Robust Cybersecurity Ethos
Instilling a robust cybersecurity ethos is paramount for your organization. Nurturing an atmosphere of open dialogue on security protocols and creating a safe space for team members to report anomalies can enhance vigilance.
Regular training updates ensure everyone stays sharp on the newest threat landscapes. With cybersecurity as a cornerstone at all echelons, your team becomes the first line of defence, safeguarding critical data and upholding the fortress that is your system’s integrity.
Conclusion
In an era where digital threats continue to grow in complexity, securing your ERP system is no longer optional—it’s a fundamental step to safeguarding your business’s future. Implementing robust security practices is essential to protecting sensitive data, enabling secure remote access, and maintaining trust with clients and stakeholders.
Adopting a high-security ERP system like HashMicro can be a game-changer in this process. With HashMicro, you’re not only choosing a secure and reliable platform but also investing in an ERP solution that seamlessly integrates all business functions, enhancing both operational efficiency and data security.
Experience firsthand how HashMicro ERP can protect and transform your business with a free demo now!